
Joanap & Brambul
On Wednesday, January 30, 2019, the United States Department of Justice announced an effort to disrupt the Joanap botnet, a network of computers infected by the Joanap malware family used to facilitate cyberattacks around the world since at least 2009.
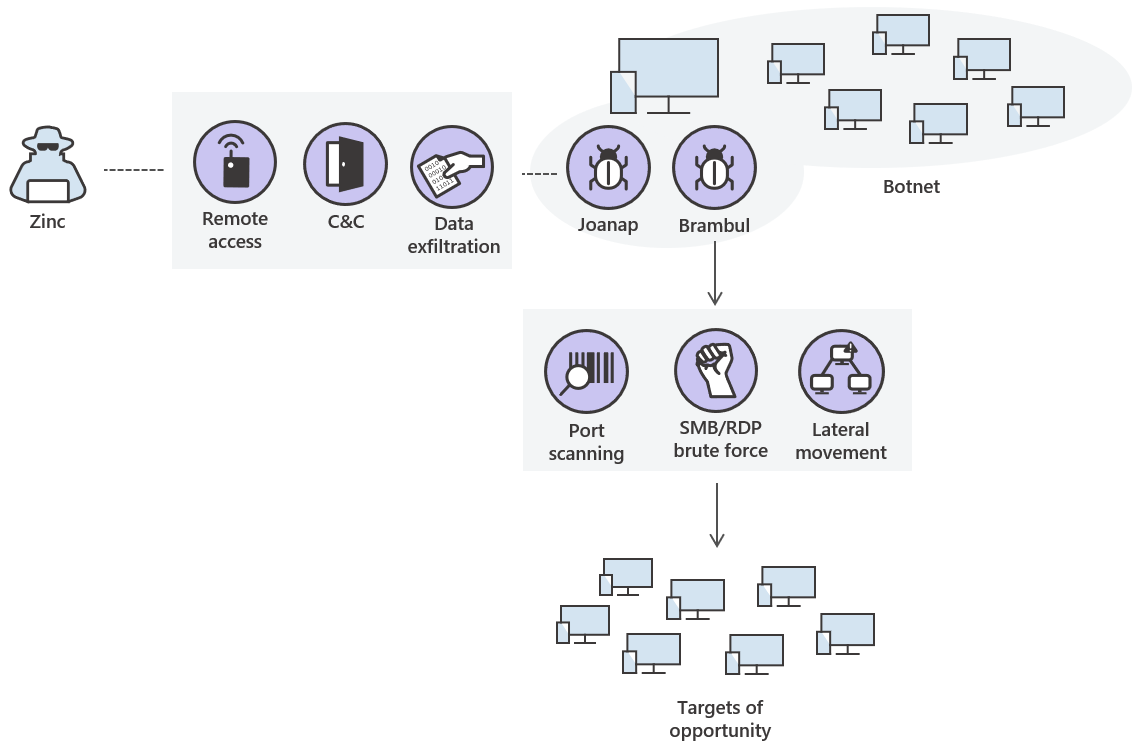
Commonly associated with the Zinc threat activity group, Joanap is a peer-to-peer backdoor that causes infected computers to communicate with each other to disseminate command and control (C&C) instructions, information about infected computers, and stolen data. It provides botnet operators with remote access to infected computers, allowing them to manage files and execute arbitrary commands. Joanap-infected computers can also be used as traffic proxies, allowing attackers to hide their real location.
In some cases, Joanap has been used to install destructive malware that cleans system data and renders computers useless.
Joanap is spread using a network-aware worm known as Brambul, which mounts brute-force password attacks against computers running the SMB protocol. In April 2017, Zinc also released a similar worm called WannaCry (detected by Microsoft as WannaCrypt) that quickly spread across the internet using the EternalBlue exploit for an SMBv1 vulnerability (CVE-2017-0144).
Applying security best practices will generally prevent infection by Brambul or Joanap. These threats, however, managed to infect networks by taking advantage of common security misconfigurations: missing patches, weak passwords, poor credential hygiene, or exposing vulnerable services to the internet.
Zinc uses Brambul to compromise targets of opportunity, scanning the Internet for open ports and performing brute-force authentication attacks. In addition to SMB, Brambul can also provide brute force RDP services.
Once Brambul achieves initial access to a machine, Joanap is deployed to maintain persistent access to the infected machine. While Brambul continues its automated attempts to find and attack vulnerable machines - both on and off the network - Joanap is used to deposit keyloggers and reconnaissance tools to capture additional credentials, enumerate the victim's network, and expand laterally. The Joanap implant is controlled by a peer-to-peer network consisting of other Joanap-infected hosts.
Zinc is a capable activity group that has been behind several high profile attacks. They are best known for committing destructive and destructive actions against their victims, such as the 2014 “Guardians of Peace” attack against Sony Pictures Entertainment or, more recently, the WannaCry ransomware attack.
Brambul and Joanap play a significant role in providing Zinc with a compromised infrastructure for these attacks.
Impact
In 2018, Microsoft registered several thousand machines with Joanap or Brambul encounters. Over the course of the same year, the number of machines with Brambul encounters steadily declined, while machines with Joanap encounters remained relatively stable and peaked in December. This pattern may be due to the use of other methods outside of Brambul to distribute Joanap.
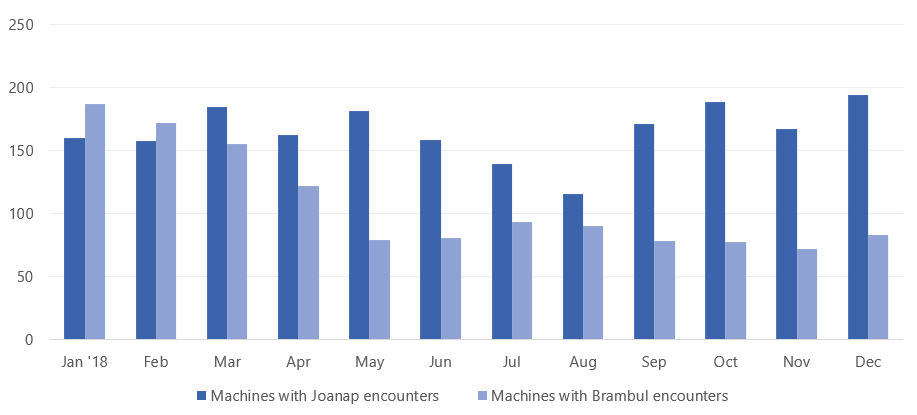
Machines with Joanap and Brambul encounters in 2018
Most dating machines were located in Taiwan, the United States, India, Japan, the Netherlands, and Italy.
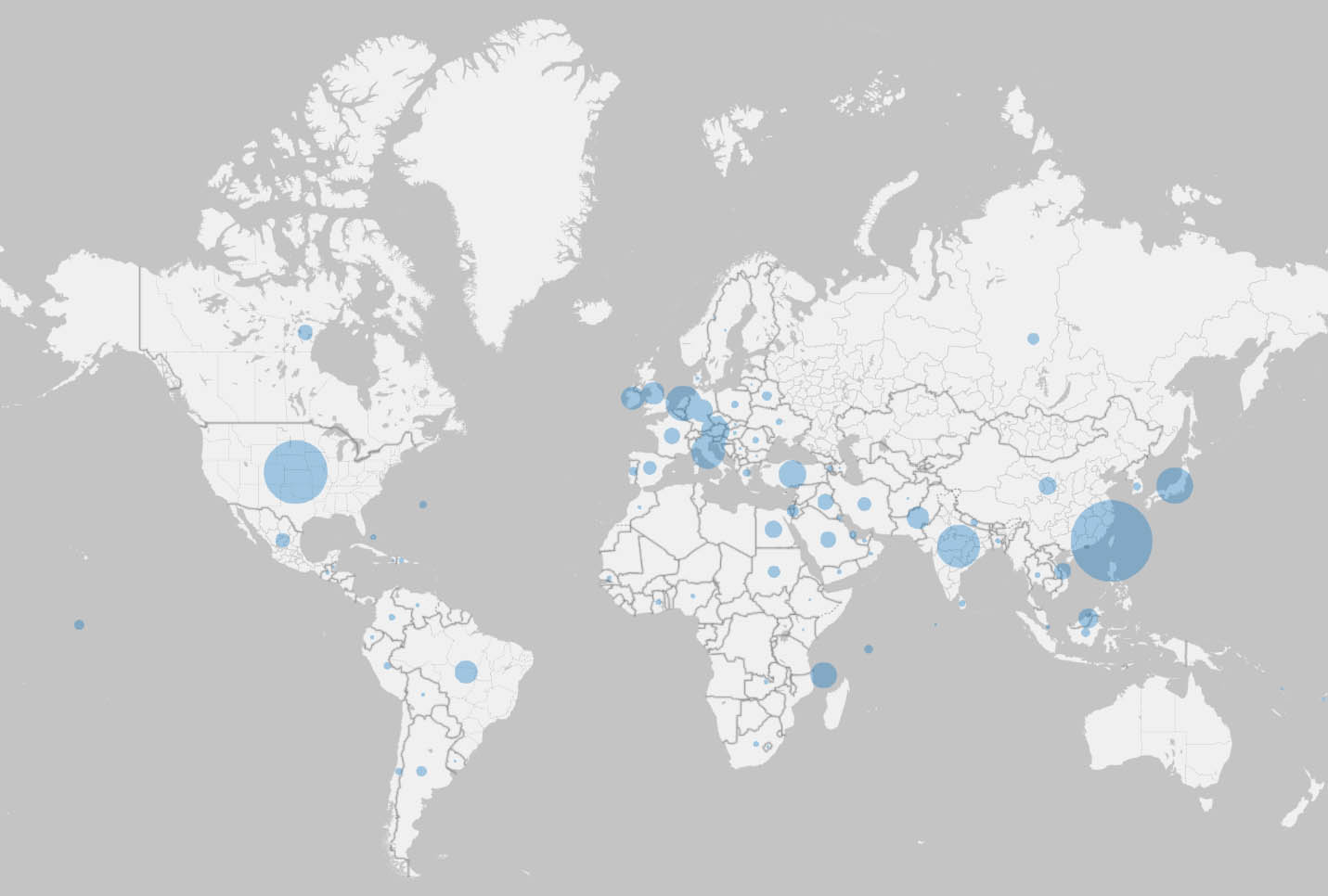
Locating machines with Joanap or Brambul encounters
Mitigations
Apply these mitigations to reduce the impact of this threat. Check the recommendations card for the implementation status of monitored mitigations.
Enable cloud-delivered protection and automatic sample submission in Windows Defender Antivirus. These capabilities use artificial intelligence and machine learning to quickly identify and stop new and unknown threats.
Use Windows Defender Firewall and network firewall to prevent RPC and SMB communication between endpoints whenever possible. This limits lateral movement as well as other attacking activities.
Avoid unnecessarily exposing SMB and other services to the Internet.
Secure Internet-facing services through a multi-factor authentication (MFA) gateway. If you don't have an MFA gateway, enable network level authentication (NLA) and verify that the server machines have strong random local administrator passwords.
Apply strong, random local admin passwords. Use tools like LAPS.

Felipe Perin
Especialista em Segurança da Informação, Entusiasta em Software Livre, Palestrante e Consultor em Preservação de Acervos. Com expertise em SIEM, Pentest, Hardening, Honeypot, WAF - Web Application Firewall, ISO 27001, SDL - Secure Development Lyfecicle, e-GOV, e-PING (Padrão de Interoperabilidade), e-MAG (Padrão de Acessibilidade), e-PWG (Administração, Codificação, Redação Web e Usabilidade), 5S, Archivematica, Atom2 - Access to Memory, OJS - Open Journal System, Virtualização, Scan de Vulnerabilidades, Data Protection Office ou Encarregado de Proteção de Dados, Monitoramento de Ativos, Backup, Resposta à Incidentes de Segurança, Gestão de Risco e Conformidade, Software Livre, Log Management, Offshore Surveyor e Projetos Ecos sustentáveis (TI-VERDE)



