
Living-off-the-land binaries
Driven by the desire to run code and remain undetected for as long as possible, attackers are constantly evolving their business art and adopting new techniques. Often, techniques originally developed for a purpose are adopted to execute malicious code in new ways. As attackers move from custom malware to evading detections, the concept of "living off the land" - using native OS executables for malicious purposes - has become increasingly common.
These techniques, many of which were originally discovered by researchers trying to bypass application whitelisting systems, leverage a level of trust not present in custom malware binaries. As a result, they often evade antivirus software and other security controls, as well as forensic investigations. While these techniques are post-exploitation and typically performed with administrative privileges already captured by exploiting or stealing credentials, they reduce the need for attackers to bring in additional tools and increase stealth.
As these techniques gain popularity in the security research community, they are also becoming increasingly popular among attackers, with new techniques regularly being publicized on social media and immediately adopted by malware campaigns. Microsoft is seeing off-the-ground binary techniques used by a wide variety of attackers with different motivations, and we are constantly improving our detection capabilities to protect customers.
Because the binary techniques of living off the land do not inherently provide elevation of privilege or additional permissions, practicing the principle of least privilege and enforcing credential hygiene can help minimize the impact of attacks. Customers who encounter these techniques on their network are advised to fully investigate the alerts, specifically because these techniques are popular with a wide class of attackers.
Analysis
While many popular Living-off-the-land binaries were developed as a means of bypassing application whitelisting solutions, it has become a popular hobby of the security research community to discover various built-in Windows binaries. that can:
Download a payload
- Run scripts or commands without using traditional shell/script hosts
- Bypass security controls such as User Account Control
- Execute code in a way that avoids traditional logging capabilities
- Provide alternate persistence points to common methods such as Windows services or registry keys
- As these binaries have legitimate uses, blocking or detecting them is not an option - attackers can use them to their advantage and detections must be behavioral, based on usage patterns.
- The use of these binaries, combined with an unintended or unexpected pattern of behavior, is in many cases a very concrete indication of malicious activity.
- Additionally, due to the well-publicized nature of these techniques, they are often, sometimes unnecessarily, used in commodity malware campaigns and automated attack frameworks. These popular uses provide researchers with additional signals that can be used to identify similar malicious activity.
Several major attacks documented by Microsoft security researchers use certutil.exe - typically used to create and submit requests to certification authorities - and regsrv32.exe, which typically register DLLs (Dynamic Link Libraries) in Windows.
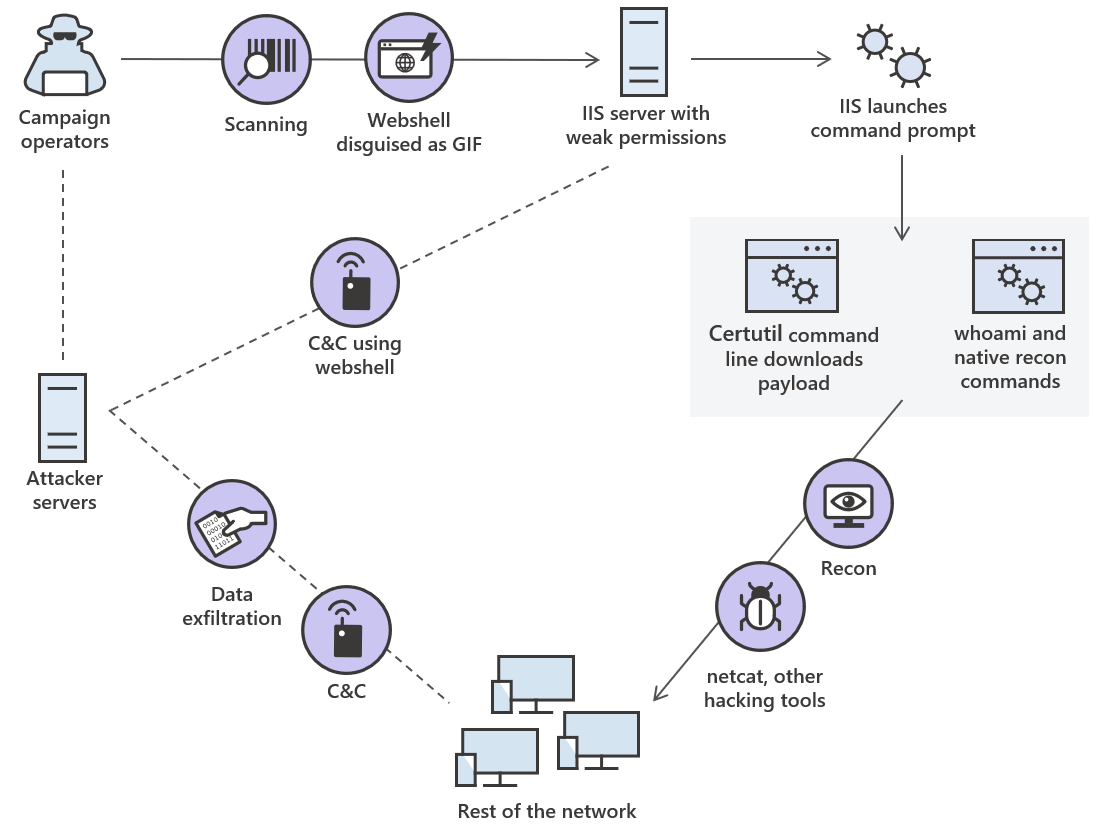
The following diagram depicts an actual attack involving certutil.exe.
During this attack, campaign operators searched for servers running Internet Information Services (IIS) with weak credentials. They installed a webshell on the servers, which allowed them to use IIS to run native recognition commands, as well as use certutil.exe to download and install Netcat and other hacking tools on other machines on the network. With hacking tools in place, operators were able to establish persistent control over multiple machines and filter data.
Mitigations
Apply these mitigations to reduce the impact of this threat. Check the recommendations card for the implementation status of monitored mitigations.
- Enable cloud-provided protection and automatic sample submission in Windows Defender Antivirus. These capabilities use artificial intelligence and machine learning to quickly identify and stop new and unknown threats.
- Practice the principle of least privilege and maintain credential hygiene. Avoid using domain-wide and administrator-level service accounts. Restricting local administrative privileges can help prevent native binaries from running with elevated privileges

Felipe Perin
Especialista em Segurança da Informação, Entusiasta em Software Livre, Palestrante e Consultor em Preservação de Acervos. Com expertise em SIEM, Pentest, Hardening, Honeypot, WAF - Web Application Firewall, ISO 27001, SDL - Secure Development Lyfecicle, e-GOV, e-PING (Padrão de Interoperabilidade), e-MAG (Padrão de Acessibilidade), e-PWG (Administração, Codificação, Redação Web e Usabilidade), 5S, Archivematica, Atom2 - Access to Memory, OJS - Open Journal System, Virtualização, Scan de Vulnerabilidades, Data Protection Office ou Encarregado de Proteção de Dados, Monitoramento de Ativos, Backup, Resposta à Incidentes de Segurança, Gestão de Risco e Conformidade, Software Livre, Log Management, Offshore Surveyor e Projetos Ecos sustentáveis (TI-VERDE)



