
Ransomware continues to hit critical healthcare services
At a time when remote work is becoming universal and the pressure on IT administrators in healthcare and critical industries has never been higher, ransomware actors are continuing business as usual. Dozens of attacks by various ransomware groups took place in the first two weeks of April 2020, targeting aid organizations, medical billing companies, manufacturing, transportation and educational software providers. While the attacks delivered varying payloads, they all used the same techniques seen in human-operated ransomware campaigns - credential theft and lateral movement, culminating in the deployment of a ransomware payload of the attacker's choice. The actions of these attackers disrupted operations at relief organizations,
While there has been a significant increase in ransomware deployments during this time, many of the compromises that enabled them have occurred earlier. For these deployments, attackers accumulate access to target networks by waiting for the ransomware to deploy during the periods they deem most beneficial to them, based on the perceived highest probability that ransom payments will be made.
Similar to the Doppelpaymer ransomware campaigns in 2019, where attackers gained access to affected networks months earlier, many of the recent attacks began by exploiting vulnerable internet-facing network devices. Other extended campaigns used brute force to compromise RDP servers. On the other hand, attacks that deliver ransomware via email tend to unfold much faster, with devices being rescued within an hour of initial entry.
Like all human-operated ransomware campaigns, these attacks exposed affected networks to serious risks that required immediate investigation and response. At some point during these attacks, campaign operators gained access to highly privileged credentials and were ready to take destructive actions if disturbed without being fully remedied. On networks where they deployed the ransomware, attackers intentionally maintained their presence on unaffected endpoints, with the intention of resuming malicious activity after the ransom was paid or systems were rebuilt.
While ransomware operators continue to compromise new targets with little regard for the critical services they affect, defenders must proactively assess risks using all available tools, including public verification solutions like shodan.io. They must also continue to enforce proven preventative solutions – credential hygiene, least privilege and host firewalls – to prevent these attacks, which have been consistently observed, leveraging security hygiene issues and over-privileged credentials.
Analysis
While the April 2020 attacks deployed multiple strains of ransomware, many of these campaigns shared infrastructure with previous ransomware campaigns. They also used the same techniques commonly seen in human-operated ransomware attacks.
To gain access to targeted networks, ransomware campaigns exploit Internet-facing systems with the following weaknesses:
- RDP or Virtual Desktop without MFA
- Older and unsupported platforms such as Windows Server 2003 and Windows Server 2008
- Citrix ADC systems affected by CVE-2019-19781
- Secure Pulse VPN systems affected by CVE-2019-11510
- Incorrectly configured web servers, including IIS, electronic health record (EHR) software, backup servers, and systems management servers
While Microsoft security researchers have not observed the campaigns described in this report exploiting the following systems, historical signs indicate that these campaigns will eventually exploit them to gain access:
- Microsoft SharePoint servers affected by CVE-2019-0604
- Microsoft Exchange servers affected by CVE-2020-0688
- Zoho ManageEngine systems affected by CVE-2020-10189
Like many breaches, attackers employed credential stealing and lateral movement capabilities in common tools including Mimikatz and Cobalt Strike. They also performed network reconnaissance and data exfiltration, remaining relatively inactive until they identified an opportune time to deploy the ransomware.
While individual ransomware campaigns and families exhibit distinct attributes, as described in the sections below, these human-operated ransomware campaigns tend to be variations on a theme. They unfolded the same way and employed the same attack techniques. Finally, the specific ransomware payload at the end of each attack chain was almost a stylistic choice made by the attackers.
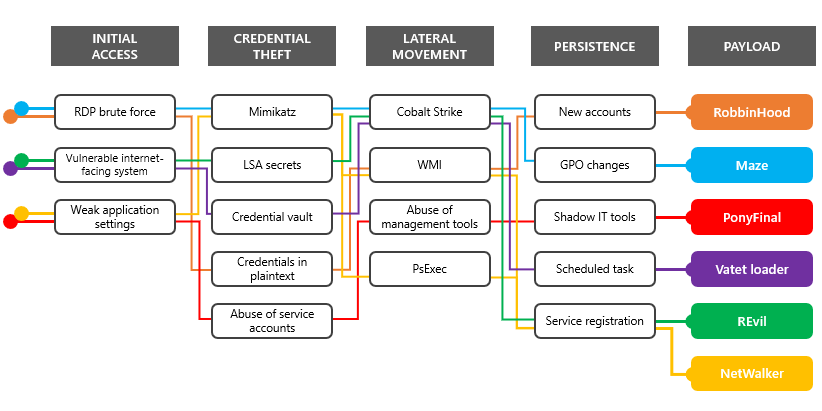
Robbinhood ransomware
operators have gained some attention for exploiting vulnerable drivers at the end of their attack chain to disable security software. However, like many other human-operated ransomware campaigns, they often start with a brute-force RDP attack against an exposed asset. They eventually get privileged credentials, mostly local admin accounts with shared or common passwords and service accounts with domain admin privileges. Robbinhood operators such as Ryuk and other well-publicized ransomware operators leave behind new local and Active Directory user accounts so that they can regain access after the malware and its tools are removed.
Vatet Loader Attackers
often change infrastructure, techniques, and tools to avoid notoriety that might attract law enforcement or security researchers. They often hold them while they wait for security organizations to start deeming the associated artifacts inactive and give them less scrutiny. Vatet, a custom loader for the Cobalt Strike framework that has been seen in ransomware campaigns since November 2018, is one of the tools that has resurfaced in recent campaigns.
The group behind this tool appears to be particularly intent on targeting hospitals in heavily affected regions, as well as aid organizations, insulin providers, medical device manufacturers and other critical verticals. They are one of the most prolific ransomware operators during this period and have caused dozens of known cases.
Using Vatet and Cobalt Strike, the group delivered several ransomware payloads. More recently, they are deploying in-memory ransomware that exploits ADS (Alternate Data Streams) and displays simplistic ransom notes copied from older ransomware families. To access target networks, they exploit CVE-2019-19781 that affects Citrix ADC systems, brute force RDP endpoints, and send email containing .lnk files that launch malicious PowerShell commands. Once on the network, they steal credentials, including those stored in the Credential Manager vault, and move laterally until they gain domain administrator privileges. The group was observed exfiltrating data before the ransomware was deployed.
NetWalker ransomware NetWalker
campaign operators gained notoriety by targeting hospitals and healthcare providers with emails claiming to provide information about COVID-19. These emails also delivered the NetWalker ransomware directly as a .vbs attachment. While this technique attracted media attention, NetWalker campaign operators also compromised entire networks to deliver the same ransomware. They abused misconfigured IIS-based applications to launch Mimikatz and steal credentials, which they used to launch PsExec.
Ponyfinal Ransomware
While this Java-based ransomware was considered new, campaigns implementing Ponyfinal were not uncommon. Campaign operators compromised Internet-facing web systems and gained privileged credentials. To establish persistence, they used PowerShell commands to launch the mshta.exe system tool and set up a reverse shell based on the common Nishang framework. They also used legitimate tools like Splashtop to maintain remote desktop connections.
Maze ransomware
One of the first ransomware campaigns to make headlines for selling stolen data, Maze continues to target technology and utility providers. Maze has a history of targeting managed service providers (MSPs) to gain access to MSP customer data and networks.
Although Maze was delivered via email, campaign operators deployed Maze on networks after gaining access using common vectors such as RDP brute force. Once on the network, they perform credential theft, move laterally to access resources and filter data, and then deploy ransomware.
In a recent campaign, Microsoft security researchers tracked Maze operators establishing access through an Internet-facing system by brute-forcing RDP against the local administrator account. Using the brute-forced password, campaign operators were able to move laterally because the built-in admin accounts on other endpoints used matching passwords.
After gaining control over a domain administrator account by stealing credentials, campaign operators used Cobalt Strike, PsExec, and other tools to deploy various payloads and access data. They established file persistence using scheduled tasks and services that launched remote PowerShell-based shells. They also enabled Windows Remote Management for persistent control. To weaken security controls in preparation for the ransomware deployment, they manipulated various settings through Group Policy.
REvil ransomware
Possibly the first ransomware group to take advantage of vulnerabilities in Pulse Secure VPN systems to steal credentials to access networks, REvil (also called Sodinokibi) has gained notoriety for accessing MSPs and accessing customers' networks and documents - and selling access to both. They maintained this activity during the COVID-19 crisis, attacking MSPs and other targets such as local governments. REvil campaigns are distinctive in adopting new vulnerabilities, but their techniques overlap with many other groups, relying on credential-stealing tools like Mimikatz once on the network and performing lateral moves and reconnaissance with tools like PsExec.
Other Ransomware
Families Other ransomware families used in human-operated campaigns during this time include:
- Paradise - the same ransomware family was distributed directly via email
- RagnarLocker - This family of ransomware is being deployed by a group heavily using RDP and Cobalt Strike with stolen credentials
- MedusaLocker - Security Signs Indicate This Ransomware Is Being Deployed Using Existing Trickbot Infections
- LockBit - this family of ransomware is distributed by operators using the publicly available CrackMapExec penetration testing tool to move laterally
Observed MITER ATT and CK
Human-operated ransomware campaigns employ a wide range of techniques made possible by attacker control over privileged domain accounts. The techniques listed here are techniques commonly used during attacks against healthcare and critical services in April 2020.

Felipe Perin
Especialista em Segurança da Informação, Entusiasta em Software Livre, Palestrante e Consultor em Preservação de Acervos. Com expertise em SIEM, Pentest, Hardening, Honeypot, WAF - Web Application Firewall, ISO 27001, SDL - Secure Development Lyfecicle, e-GOV, e-PING (Padrão de Interoperabilidade), e-MAG (Padrão de Acessibilidade), e-PWG (Administração, Codificação, Redação Web e Usabilidade), 5S, Archivematica, Atom2 - Access to Memory, OJS - Open Journal System, Virtualização, Scan de Vulnerabilidades, Data Protection Office ou Encarregado de Proteção de Dados, Monitoramento de Ativos, Backup, Resposta à Incidentes de Segurança, Gestão de Risco e Conformidade, Software Livre, Log Management, Offshore Surveyor e Projetos Ecos sustentáveis (TI-VERDE)



