
Ryuk ransomware
Ryuk is part of a series of prevalent and highly destructive human-operated ransomware campaigns that have gained significant notoriety in recent years. By causing significant downtime and business disruption, as well as demanding massive ransom payments, these campaigns continue to wreak havoc on numerous organizations including corporations, local governments and non-profits.
Reports on Ryuk and many other human-operated ransomware attacks have focused on downtime, ransom payments, and the details of the ransomware payload itself. However, they rarely discuss the long-running campaigns and avoidable total domain compromises that enabled them.
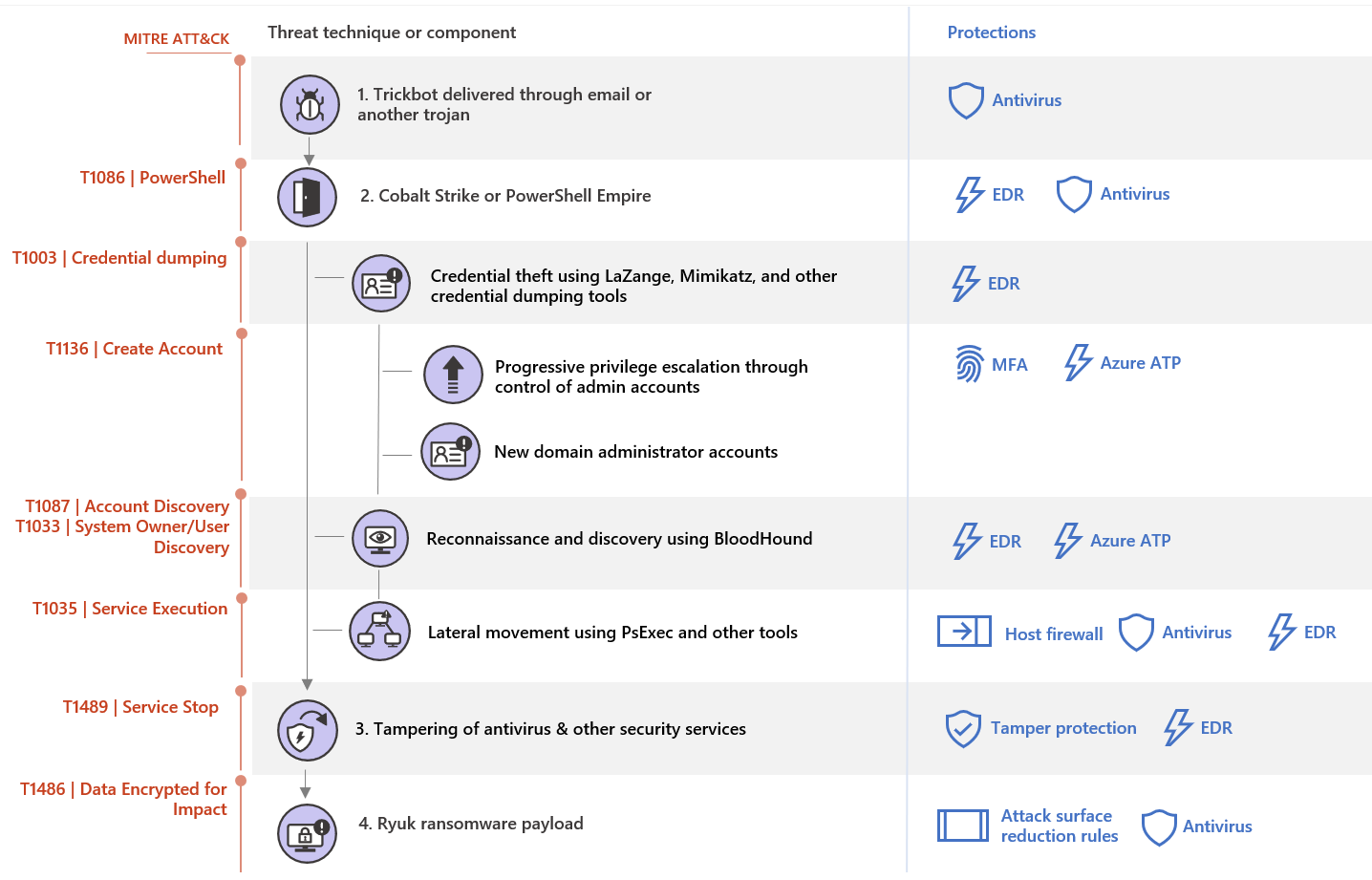
Like Doppelpaymer, Ryuk was recently in the final stages of an infection with a banking Trojan like Trickbot. Likewise, Trickbot itself can be introduced by Emotet or another trojan, although it has also been distributed directly via email.
Before a Ryuk infection occurs, an existing Trickbot implant typically downloads a new payload, such as Cobalt Strike or PowerShell Empire, and starts moving laterally within the network. This specific behavior indicates that campaign operators typically leave Trickbot infections dormant until they have screened the next set of target endpoints for the next stages of the attack.
In some organizations, Trickbot infections are often considered low-priority threats and are not patched and isolated with the same degree of scrutiny as other higher-profile malware. This works in the attackers' favor, allowing them to establish persistence across a wide variety of networks. Trickbot and Ryuk operators also take advantage of users running as local administrators and use these permissions to disable security tools that would otherwise prevent their actions.
Once Ryuk operators are active on a network, they utilize traditional lateral movement techniques involving credential theft and reconnaissance with tools like BloodHound to eventually take over a domain administrator account. They also often add an innocuous-named account to Active Directory as an additional backdoor and grant domain administrator privileges so that account can deploy ransomware.
To deploy Ryuk, operators used PsExec, Group Policy, and init scripts that load the SYSVOL share payload. Additionally, they sometimes selectively choose not to deploy Ryuk or any other ransomware on endpoints that have Cobalt Strike or other persistence mechanisms. Instead, they can inspect files and exfiltrate data from these machines. This sophisticated behavior highlights the need to fully investigate Ryuk ransomware infections and enforce the entire incident response process.
Attack techniques and components
Ryuk originated as an email-delivered ransomware payload and has since been adopted by human-operated ransomware operators. Ryuk is one of the possible payloads delivered by carriers that enter networks initially using Trickbot infections. An existing installation of Trickbot - whether delivered directly via email or dropped by Emotet - is activated by downloading a Cobalt Strike or PowerShell Empire beacon as a payload. These tools give operators more maneuverability and lateral movement options on the network. While these are familiar tools for attackers, their popularity among penetration testers may allow them to blend in and hide behind the red team's expected activities.
On many networks, Trickbot activation often occurs well after the initial infection.
Once campaign operators are active, they use Cobalt Strike or PowerShell to initiate reconnaissance and lateral movement. They often start by using built-in commands such as netgroup to enumerate the membership of domain administrators, enterprise administrators, and other privileged groups. They use this information to identify targets for credential theft.
Ryuk operators then use a variety of techniques to steal credentials, including using the LaZagne Credential Stealing Tool and saving entire hives from the registry to extract credentials from the Local Accounts and LSA Secrets parts of the registry. They take advantage of passwords for service accounts and scheduled tasks configured to automatically start with a predefined account. On some networks, security services and systems management software are often configured to run with excessive privileges in the context of domain administrator accounts, making it very easy for Ryuk operators to jump from a desktop to a class-based system. server or domain controller.
In some environments, after performing initial basic reconnaissance and credential theft, campaign operators utilize the open source security audit tool known as BloodHound to gather detailed information about the Active Directory environment and potential attack paths. They likely retain the data collected during these stages after the ransomware is deployed.
Ryuk's operators then continue to move laterally to higher value systems, inspecting and enumerating files of interest as they go along, possibly infiltrating that data. Attackers then gain domain administrator privileges and use elevated permissions to deploy the ransomware payload. They often use domain administrator credentials stolen from interactive logon sessions on a domain controller. They have been seen deploying ransomware using Group Policies, startup items on the SYSVOL share or, more commonly in recent attacks, PsExec sessions emanating from the domain controller itself.
Deployment of ransomware often occurs weeks or even months after any initial attacker activity on the network.

Felipe Perin
Especialista em Segurança da Informação, Entusiasta em Software Livre, Palestrante e Consultor em Preservação de Acervos. Com expertise em SIEM, Pentest, Hardening, Honeypot, WAF - Web Application Firewall, ISO 27001, SDL - Secure Development Lyfecicle, e-GOV, e-PING (Padrão de Interoperabilidade), e-MAG (Padrão de Acessibilidade), e-PWG (Administração, Codificação, Redação Web e Usabilidade), 5S, Archivematica, Atom2 - Access to Memory, OJS - Open Journal System, Virtualização, Scan de Vulnerabilidades, Data Protection Office ou Encarregado de Proteção de Dados, Monitoramento de Ativos, Backup, Resposta à Incidentes de Segurança, Gestão de Risco e Conformidade, Software Livre, Log Management, Offshore Surveyor e Projetos Ecos sustentáveis (TI-VERDE)



